5. DETERMINING THE OPTIMAL COMMUNICATION PROTOCOL
5.1 The Optimization Problem
The optimization problem faced by X and Y in designing the communication protocol can be stated as follows:
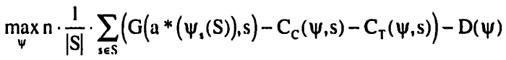
This turns out to be a difficult problem to solve in general since the protocol space is both discrete and large. First, the number of possible partitions grows exponentially with the size of the state space11. Second, for most non-trivial partitions, there are several different protocols that induce the partition but have different costs.
The overall strategy for solving this optimization problem is as follows. First a simple example will be used to illustrate the problem (in Section 5.2). Second, the benefits (in Section 5.3) and costs (in Section 5.4) of bisections are analyzed in order to determine an optimal bisection (in Section 5.5). Third, the understanding of optimal bisections is used to construct optimal protocols (in Section 5,6).
11 It is easy to see that 2|S|-1 is a lower bound on the number of partitions.
5.2 Example
Consider the state space S = {,2,3,4,5, 6, 7,8} together with the action space A = {1,1,5, 2, 2,5,....,7,5,8}. Assume the following benefit function:
G(a, s) = 10-(a-s)2
Given the assumptions from Section 4, it is now possible to determine both the benefit and the cost of a bisection. Without any information, i.e. for the uniform distribution, the optimal action for Y is to choose a*(S) = 4.5. Doing so results in an expected benefit of
10 - l/8.(3.52+2.52+1.52+0.52+0.52+1.52+2.52+3.52) = 10 - 5.25 = 4.75
Consider the first bisection. It is easy to see that the optimal bisection for improving the expected benefit would be Ex = jl, 2,3,4} and E2 = {5,6, 7,8|. The optimal choices of actions are then a*(Ei) = 2.5 and a*(E2) = 6.5 respectively, resulting in an expected benefit of
10 - [l/2.1/4.(1.52+0.52+0.52+1.52) + l/2-l/4.(1.52+0.52+0.52+1.52)] = = 10-1.25 = 8.75
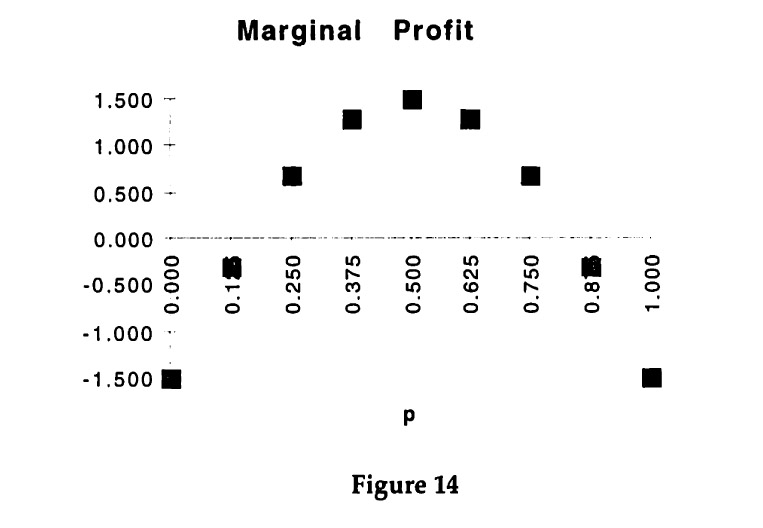
A convenient way for summarizing the possible improvements in expected benefit is to graph the marginal benefit for different probabilities of bisections. If the bisection of E is E1 and E2, let p = |E1 | / |E|. For each p several different bisections are possible, but only the one with the highest marginal benefit12 will be considered. For example, for p = 1/2 only the bisection into {1, 2,3,4} and {5,6, 7, 8} is considered instead of other bisections, such as {1, 2, 7, 8} and {3,4, 5, 6}. This method results in the following graph:
12The marginal benefit should properly be referred to as marginal expected benefit, but the "expected" is omitted for brevity.
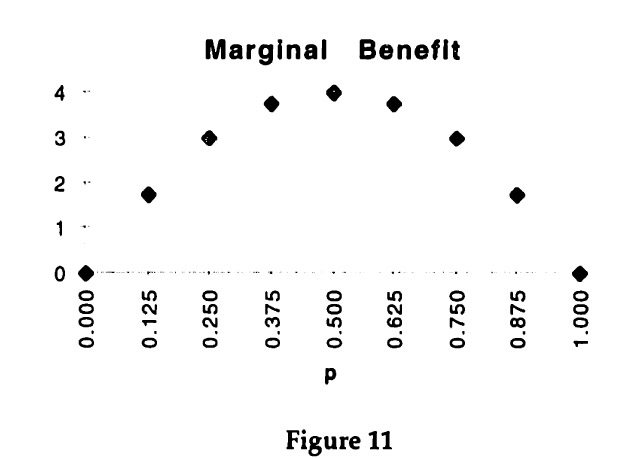
Using the assumptions about the cost of communication from above, it is also possible to determine the cost of the first bisection of the state set. Suppose that the protocol tree Ψ consists only of this first bisection, then the cost are as follows
- D(Ψ) = d
- Cc(Ψ, s) = cc.h(p) for all s Є S
- CT(Ψ, s) = cT + γT for all s Є S
The cost that has to be subtracted from the benefit of the bisection for each use of the communication protocol is Cc(Ψ, s) + CT(Ψ, s).
The graph is based on assuming cT = 0.5, γT = 1.0, and cc = 1.0. The cost of design is not included and will be considered separately later on.
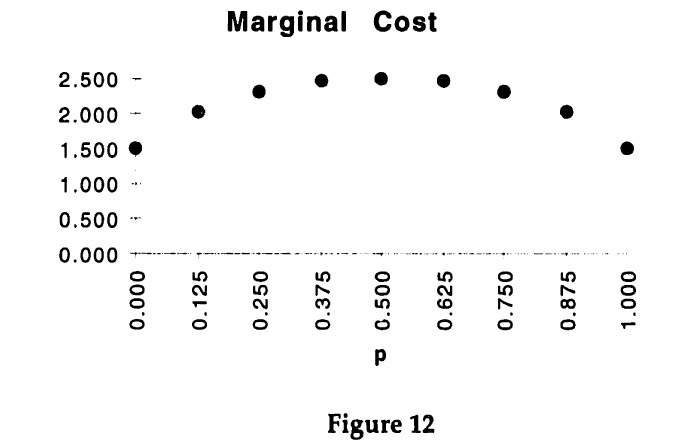
The difference between the marginal benefit and the marginal cost of using the protocol is the marginal profit.
As can be seen from Figure 13, the maximal marginal profit from the first bisection occurs for p = 0.5, i.e. when the two resulting subsets are of equal size. The optimal subsets are {1,2, 3,4} and {5,6, 7, 8}. This can also be seen by graphing the marginal profit directly, as in Figure 14.
Having determined the optimal first bisection for Example 1 raises a number of key questions that will be answered in the following sections.
Ql How can optimal bisections be determined generally?
Q2 When does the optimal bisection occur for p ≠ 0.5?
Q3 How can optimal bisections be used to describe an optimal protocol?
The answers to these questions will then be used to explain some anecdotal evidence on communication in organizations.
5.3 Marginal Benefit from a Bisection
The first issue in determining an optimal bisection is to consider the marginal benefit from choosing a particular bisection. Let Ψ(S) be the partition induced by the current communication protocol. Let E Є Ψ(S) and consider a bisection of E into E1 and E2 that results in a finer partition Ψ'(S). The marginal benefit from this additional bisection is given by
The marginal benefit has a number of interesting properties which will now be examined.
| Bl |
The marginal benefit must be non-negative, i.e. b(E, E1) ≥ 0 since choosing the optimal action a* for smaller subsets amounts to relaxing a constraint: it is always possible to choose the same action for both E1 and E2 that would have been chosen for E. The marginal benefit will also be bounded, since it is a finite sum of bounded values (given the assumption made throughout that the benefit function G(a, s) is bounded for all actions and all states). |
| B2 |
The marginal benefit can be highest for a splitting out a singleton. Consider, for instance, S = {1, 2,... n} and A = S with the benefit given by
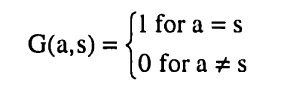
By inspection, it follows that the marginal benefits of a bisection are given by the following expression:
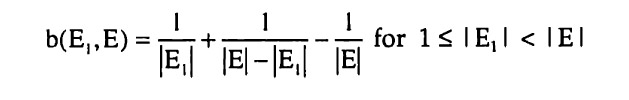
The expression is maximized by |E1 | = 1 and by |E1| = |E| - 1. In either case, the marginal benefit is maximal for a bisection that splits out a singleton, More generally, splitting out singletons will be optimal when the only available actions are highly specific to a particular state, i.e. have a benefit only in that state. |
| B3 |
The marginal benefit from bisections can be increasing. Consider the following example where S = (1,2,3} and A = {1,2,3,4). Let the benefit be given by the following matrix:
Without any communication, the optimal action is a*{l, 2,3} = 4, resulting in an expected payoff of 0. With the first bisection it becomes possible to split out one of the states, e.g. Ψ(S) = {{1}, 12,3}}. The optimal actions are a*({l}) = 1 and a*({2,3}) = 4 and the marginal benefit is
b({l, 2,3}, {1}) = 1/3 . 3 + 2/3 . 0 - 3/3 . 0 = 1
The second bisection splits {2,3} into {2} and |3). The optimal actions are a*({2}) = 2 and a*({3}) = 3 and the marginal benefit is
b({2,3}, {2}) = 1/3 . 3 + 1/3 . 3 - 2/3 . 0 = 2
The marginal benefit for the second bisection is thus larger than the one from the first bisection. More generally, the marginal benefit is likely to be increasing when there are some specific actions that have high benefits for some specific states but do poorly in all other states, whereas other actions have moderate benefits across many states. |
| B4 |
The marginal benefit from bisections can also be decreasing. Consider the earlier example with S = (1,2,3, 4,5,6,7,8), A = (1,1.5,2,2.5 ... 7.5,8} and G(a, s) = 10 - (a - s)2. The marginal benefit from the first bisection was
b({l, 2,3,4,5,6,7,8}, {1,2,3,4}) = 8.75 - 4.75 = 4
Subsequent bisections have lower marginal benefits, e.g.
b({l, 2,3,4}, {1, 2}) = 2/8 . [10 - 0.52] + 2/8 . [10 - 0.52] -- 4/8 . [10-1/4 . (1.52 + 0.52 + 0.52 + 1.52)] = 1/2
and
b({l, 2},{1})= 1/8 .10 + 1/8 . 10 - 2/8 . [10 - 0.52] = 1/16
More generally, when there are state-specific actions, for which the benefits do not decrease too rapidly for other states, then the marginal benefit of bisections will be decreasing. |
| B5 |
The marginal benefit from bisections always drops to zero eventually. This property can be seen by considering the following definition.
Definition: A constant action subset is a subset E of S, such that one constant action a Є A is optimal for every state s Є E
It follows immediately from the definition that if E is a constant action subset then b(E, E1) = 0 for all subsets E1 of E, Hence, as soon as a partition is sufficiently fine to consist of constant action subsets only, the marginal benefit of a subsection will be zero. At the latest, a partition of all singletons will always have zero marginal benefit.13 |
In order to see how these properties affect the optimal protocol it is now
necessary to examine the marginal cost of a bisection.
5.4 Marginal Cost of a Bisection
5.4.1 Strategy
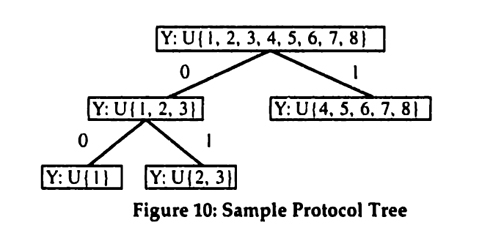
Determining the marginal cost of a bisection turns out to be more difficult than determining its marginal benefit. To understand why, consider the following example. Suppose that S = {1,2,3,4,5,6,7,8} as before. Assume that the current partition is Ψ(S) = {{1}, {2,3,4,5,6,7,8}}. What is the incremental cost of bisecting E = {2,3,4,5,6,7,8} into El = {2,3} and E2 = {4,5,6,7,8}? This is difficult since there are several possible protocols. Figure 15 and Figure 16 below show two possibilities.
13Constant action subsets will generally be larger than singletons. In fact, whenever |S| > |A|, there has to be at least one constant artion subset that is larger than a singleton. This follows because for every state there has to be at least one optimal action and if there are more states than actions, at least two states have the same optimal action.
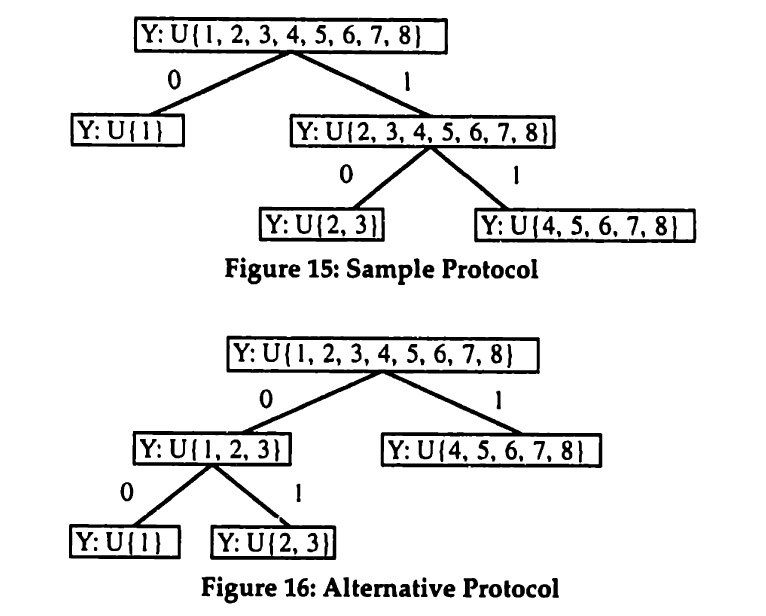 Figure 15 shows the protocol Ψ1 that would result if one took the existing protocol Ψ and extended it with the additional bisection. Figure 16 (which is a reproduction of Figure 10) shows another protocol Ψ2 that implements the same partition.
Consider the various cost components. First, the design cost is clearly the same for both protocols since both have two internal nodes. Second, the cost of coding can be calculated as follows:
E[Cc(Ψ1, S)] = cc . [1 . h(l/8) + 7/8 . h(2/7)] = cc . 1.29879494
E[Cc(Ψ2, S)] = cc . [1 . h(3/8) + 3/8 . h(l/3)] = cc . 1.29879494
This equality will be seen not to be a coincidence.14 Third, the cost of transmission is as follows:
E[CT(Ψ1, S)] = cT . [1.1 + 7/8.2] + γT = cT . 2.75 + γT
E[CT(Ψ2, S)] = cT . [1.1 + 3/8.2] + γT = cT . 1.75 + γT
Clearly, the transmission cost for protocol Ψ2 are lower than for protocol Ψ1
Hence the marginal cost of the bisection should be determined as the difference between the cost of the protocols Ψ2 and Ψ . The strategy for determining the marginal cost of a bisection will be as follows. First, a cost minimizing protocol is developed for an arbitrary partition (Section 5.4.2).
14See Section 5.4.2 below and Appendix Al.
Second, the marginal cost of a bisection is determined as the difference in cost between two cost minimizing protocols (Section 5.4.3).
5.4.2 Least Cost Protocol
Let P(S) be an arbitrary partition of S. The objective in the first step is to find a protocol Ψ with minimal cost of communication, such that Ψ(S) = P(S).15 Consider the following algorithm for designing a protocol based on Huffman coding.16 The notation Root(Ψ) refers to the set associated with the root of the binary tree Ψ (e.g. in Figure 15, Root(Ψ) = {1,2,3,4,5,6, 7,8}).
Least-Cost Protocol (LCP) Algorithm
- Let each subset s ∈ P(S) be a partial binary tree Ψ, consisting of a single node, i.e. Root(Ψ) = s.
- Sort all partial trees according to their frequency, which is given by | Root(Ψ) |, i.e. the size of the set at their root node.
- Combine the two least frequent partial trees Ψ' and Ψ" into a larger tree Ψ so that Root(Ψ) = Root(Ψ') ∪ Root(Ψ").
- Repeat Steps 2 and 3 until there is only a single tree Ψ left.
Consider, for example, S = {1,2,3,4,5,6,7} and P(S) = {{1,2}, {3,4,5}, {6,7}}. The LCP Algorithm constructs a protocol tree as illustrated in Figure 17 below.
15This equality is a slight abuse of notation since both Ψ(S) and P(S) are sets of sets. Properly this should be written as P(S) ⊇ Ψ(S) and Ψ(S) ⊇ P(S).
16 This type of coding was introduced by Huffman (1952). For an introduction see Cormen, Leierson et al. (1990).
It will now be shown that this algorithm minimizes the cost of designing and using a protocol tree that implements the desired partition.
Proposition: Let P(S) be an arbitrary partition of S. Then the LCP
Algorithm finds the protocol Ψ which induces the partition Ψ(S) = P(S) at the minimal cost of designing and using the protocol.
Proof: First, consider the cost of protocol design. By inspection, the LCP algorithm creates a binary tree that induces the partition P(S). Since LCP creates a full binary tree,17 the number of internal nodes is minimized and is equal to | P(S) -I| The minimized cost of design is thus
D(Ψ) = d . (|P(S)|-l)
Second, consider the cost of coding. Given the assumptions, a simple inductive argument (see Appendix Al) shows that the expected cost of coding is determined entirely by P(S) for any protocol that implements P(S). Independently of the protocol structure, the expected cost of coding is
E [Cc(Ψ,s)] = cc . H[P(S)]
where H[ . ] is the entropy of the partition P(S). Given the assumption of a uniform distribution, the expression for the entropy is
17 In a full binary tree, every internal node has two children.
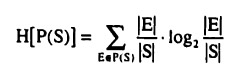
Third, consider the cost of transmission. As first shown by Huffman (1952), the LCP algorithm minimizes the expected path length. It hence also minimizes the cost of transmission, which is a linear function of the path length. The expected length of the path is bounded by H[P(S)] below and H[P(S)]+1 above so that the expected variable cost of transmission is
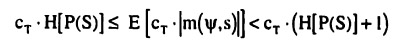
LCP thus minimizes the cost of communication.
Two results from the proof are of particular importance. First, both the cost of design and the cost of coding are seen to be independent of the protocol structure, as long as the binary tree induces the desired partition. Only the cost of transmission determines the protocol structure. Second, the proof provides expressions for the minimized cost. For the cost of transmission, however, only a range was specified since there is no closed form for the exact expected path length. For simplicity, it will be assumed that the lower bound is achieved, so that the total cost of transmission is
E[CT(Ψ,s)] = CT.H[P(S)] + γT
This assumption can be justified in two ways. First, if communication is repeated, then the lower bound is achievable as a limit by a similar algorithm (Huffman 1952). Second, the expected length is generally closer to the lower bound, except for distributions that put almost the entire weight on a few elements of the partition. In the latter case, a slight modification of the protocol—which will be discussed below (see Section 6.2)—results in an expected length close to the lower bound.
5.4.3 Marginal Cost of a Bisection
The marginal cost of a bisection can now be determined as the difference between the minimized cost for two partitions. Let P(S) be an arbitrary partition of S and let P'(S) be the partition that results from the additional bisection of E ∈ P(S) into the subsets E1, and E2. The marginal cost of design is simply the cost of adding an internal node to the protocol. Focusing on the cost of coding and the cost of transmission results in the following marginal cost.
c(E, El) = (cc + cT).{H[P'(S)]-H[P(S)]}
This expression can be simplified as follows:
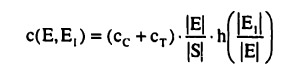
The marginal cost has a number of interesting properties which will now be examined.
| C1 |
The marginal cost is strictly positive as long as cc > 0 or cT > 0. So even if communication technology were to reduce the cost of transmission to zero, the cost of coding would still result in a positive marginal cost. While the two cost components are simply additive in the expression for the marginal cost, they differ in their effect on the communication protocol. In the proof it was shown that only the cost of transmission affects the structure of the optimal protocol whereas the cost of coding was found to be constant across protocols. This difference will be seen to have implications for the effect of technology on communication protocols. |
| C2 |
The marginal cost is highest when splitting large subsets evenly. While this obviously reflects the assumptions, it also fits nicely with the intuition that the marginal cost should be highest for the highest reduction in uncertainty. As can be seen from the expression, the marginal cost is higher, if a larger subset is being bisected (the |E| / |S| term) since the cost of coding and transmission have to be incurred more frequently. The marginal cost is also higher, if the bisection is more symmetrical and hence results in a larger reduction of uncertainty (the h(.) term). |
| C3 |
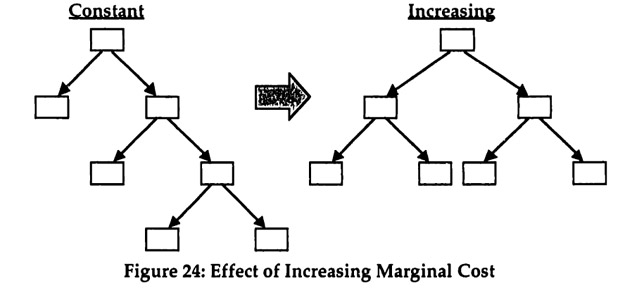
The marginal cost of a bisection is decreasing. With more bisections, the size of the subsets in the partition decreases and hence the |E| / |S|term decreases towards 1/ |S| since bisections of smaller subsets are moved further down in the protocol tree by the LCP algorithm and hence occur less frequently. This property is the result of the assumption of constant marginal cost per message segment and per coding question. Clearly, these assumptions require further study. In particular, the effects of time constraints and congestion need to be explored.18 |
18 Time constraints, congestion of communication channels, and bounded rationality of the team members could result in increasing marginal cost for coding and transmission. This possibility is discussed in Section 7.
5.5 Optimal Bisections
Based on the marginal benefit and marginal cost of a bisection it is now possible to determine and characterize optimal bisections. An optimal bisection maximizes the marginal benefit net of marginal cost. Let E be an element of the current partition Ψ(S). Then the optimal bisection of E into E1* and E2* is determined by
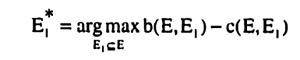
and E2* = E \ E1*. The expressions for b(E, E1) and c(E, E1) were derived in Sections 5.3 and 5.4 respectively.
These results can now be used to answer the first two questions raised at the end of Example 1 in Section 5.2:
Ql How can optimal bisections be determined generally?
Al Find the marginal benefit function b(E, E1) and the marginal cost function c(E, E1) and use them to determine E1* and E2*.
and
Q2 When does the optimal bisection occur for p ≠ 0.5?
A2 The optimal bisection occurs for p = 0.5 only for symmetric and
sufficiently concave marginal benefit functions. Consider the marginal benefit function from the example used in characterization B2 (in Section 5.3), which is convex and maximal for splitting out a singleton. Given that the marginal cost function is always concave, the optimal bisection will split out a singleton.
The next section takes up the third question by examining how this knowledge of optimal bisections can be used to characterize optimal protocols.
5.6 Characterizing Optimal Protocols
5.6.1 Strategy
The understanding of the marginal benefits and costs of bisections developed above will now be used to characterize optimal protocols. The optimal protocols for the case of costly communication will be contrasted with the case of free communication. First, some weak but quite general characterizations will be given without imposing any restrictions on the benefit function (Section 5.6.3).
Second, exact optimal protocols are determined and characterized for restricted benefit functions (Section 5.6.4).
5.6.2 Free Communication
The case of free communication will be used as the benchmark for examining the effects of communication cost. It is characterized in the following proposition.
Characterization: The case of free communication, i.e. d, cc, cT, γT. = 0, has the following features
(i) any protocol that partitions the state set S into singletons is optimal,
independent of the benefit function G(a, s);
(ii) it is possible for the recipient Y to choose the optimal action for
every realization of the state s Є S.
Proof: Since all protocols are costless, the team members can choose a protocol y that partitions S into singletons. After communication has taken place, the action is chosen according to
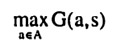
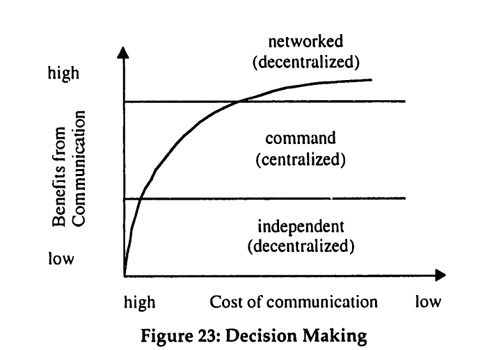
which results in the choice of the optimal action for every realization of s. It is therefore not necessary to know G(a, s) when designing the protocol. □ These features have an important interpretation: for a given state set S, the team members X and Y can design a single protocol that partitions S into singletons. This general purpose protocol can then be used by X and Y for any communication, independent of the particular decision. It is important to note that coordination on a protocol is still required, even when communication is free.19 Furthermore, a partition into singletons amounts to team member X providing Y with all the available information. Y then chooses the optimal action based on the information and carries it out. This arrangement can be interpreted as decentralized decision making, since the decision which action to choose is made by the team member who has to take the action.
19 There are many different protocols that result in a partition of all singletons and without prior agreement on one of these protocols, no communication is possible.
5.6.3 Costly Communication with General with General Benefits Functions
Based solely on the properties of the marginal benefit and marginal cost derived so far, it is possible to give a weak characterization of optimal communication protocols with costly communication.
Characterization: The case of costly communication, i.e. d, cc, cT, γT. = 0, has the following features
(i) optimal partitions depend on the benefit function G(a, s) and never
include two elements E1 and E2, such that E = E1 U E2 is a constant
action subset;
(ii) for sufficiently high cost of communication, it may not be possible
for the recipient Y to choose the optimal action for every realization of
the state s Є S;
(iii) small changes in the cost of communication can result in large
changes in the amount of communication.
Proof: The marginal cost of communication is strictly positive (CI) and the marginal benefit from bisecting a constant action subset is zero (B5). Hence constant action subsets are never bisected. This establishes feature (i) since the constant action subsets are determined by the benefit function G(a, s).
There are two ways of showing feature (ii). First, since the marginal benefit is bounded (Bl), if the cost of communication is sufficiently high, then there will be no communication at all. In this case, the recipient Y has to base the choice of action solely on the prior information of a uniform distribution over the states. Except for the trivial case in which the same action is optimal for all states, Y thus cannot choose the optimal action for every realization. Second, feature (ii) also emerges when the marginal benefit of bisections declines (B4) more rapidly than the marginal cost of bisections (C3). In this case too, the optimal partition will contain elements that are not constant action subsets, hence making it impossible for Y to choose the optimal action for all realizations.
Finally feature (iii) occurs in situations where the marginal benefits of bisections are increasing (B3). Suppose that initially the marginal cost of bisections is simply too high for any communication to occur at all. Since the marginal cost of bisections is decreasing (C3), if the marginal cost ever drops below the marginal benefit, it will stay below for subsequent bisections. Hence in such a situation, as the cost of communication declines, the optimum will jump from no bisection immediately to a partition into constant action subsets. □
These features provide an interesting contrast with those for the case of free communication. First, with costly communication the team members can not use a general purpose protocol. Instead, different decision situations require different protocols. Second, in some situations, the optimal protocols can be interpreted as centralized decision making with the use of commands, X observes a realization of s and decides on the optimal action, which is then communicated to Y as a command. In this interpretation each constant action subset of the optimal partition corresponds to a different command, i.e. X simply tells Y which action to take. This interpretation is discussed in greater detail in one of the applications below.
5.6.4 Costly Communication with Restricted Benefit Functions
So far, the crucial third question, how optimal protocols can be constructed, has not been answered. The approach pursued here is a "greedy algorithm" (Cormen, Leierson et al, 1990). Starting with the set S, a sequence of optimal bisections is chosen one bisection at a time. Instead of looking ahead, a greedy algorithm is myopic and only optimizes the next step. The advantage of a greedy algorithm is that the characteristics of the optimal protocol follow directly from the characteristics of optimal bisections, which have been determined above.
Depending on the particular optimization problem, there may or may not exist a greedy algorithm that finds an overall optimal solution. Put differently, a sequence of optimal steps may or may not result in an optimal path. The question then is whether a sequence of optimal bisections results in an optimal protocol. Unfortunately, a greedy algorithm for general benefit functions is not possible, as counterexamples can easily be constructed (see Appendix A2 for an example)20. Instead of a general proof, the strategy therefore is to show that a greedy algorithm exists for interesting cases of benefit functions.
For a greedy algorithm to result in the optimal protocol, two properties have to hold, the Greedy Property and the Optimal Substructure Property (Cormen, Leierson et al. 1990).
20 Strictly speaking the counterexample only establishes that a greedy algorithm based on the particular metric for optimal bisections does not exist. There might be a greedy algorithm using a different metric or even a different set of steps.
Greedy Property: For any optimal partition Ψ(S), there exists at least one sequence of bisections that results in Ψ (S) and that starts with the optimal bisection of S.
Optimal Substructure Property: Any subset of an optimal partition Ψ (S) is itself an optimal partition for the proper subset of S.
For a given benefit function, the challenge is to show that both properties hold. The strategy for proving the Greedy Property is quite straightforward. The proofs starts by noting that a sequence of bisections can be reordered arbitrarily and still results in the same partition. Starting with an optimal partition, it is assumed that no sequence of bisections exists results in the optimal partition and contains the optimal first bisection anywhere. This assumption is then shown to lead to a contradiction with the assumed optimality of the sequence. The Optimal Substructure Property amounts to a regularity condition on the benefit function. The available actions and the structure of the benefits has to be similar for subsets of the states. In the examples considered below, the Optimal Substructure Property will follow immediately from the restrictions on the benefit function.
Suppose now that the two properties have been shown to hold for a particular benefit function. The characteristics of the optimal protocol can then be derived from the characteristics of an optimal bisection, which answers the third question raised in Section 5.2:
Q3 How can optimal bisections be used to describe an optimal protocol?
A3 If the greedy property and the optimal substructure property hold, a sequence of optimal bisections will result in an optimal protocol.
For example, if the optimal bisection splits out a single state, then as the cost of communication drops, the optimal protocol will consist of an increasing number of individually identified states. The discussion of anecdotal evidence in the next section contains concrete examples of benefit functions for which both properties hold. |
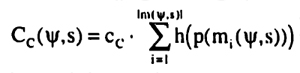
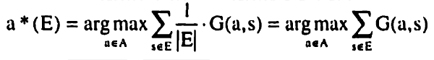
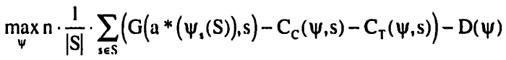
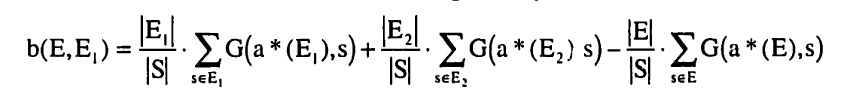
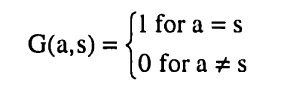
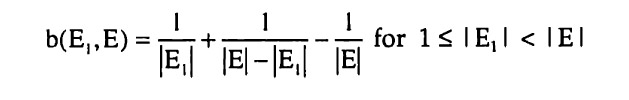
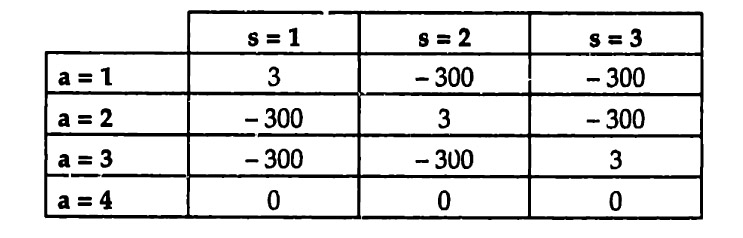


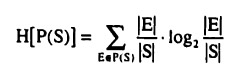
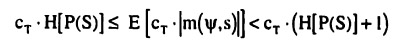
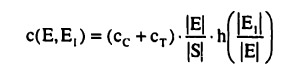
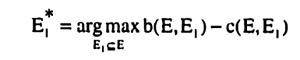
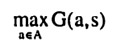
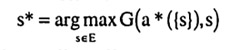
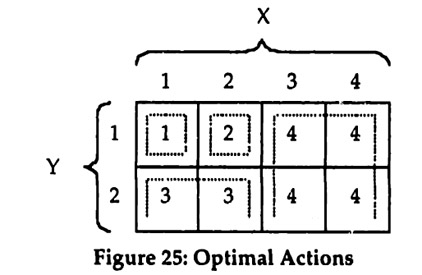
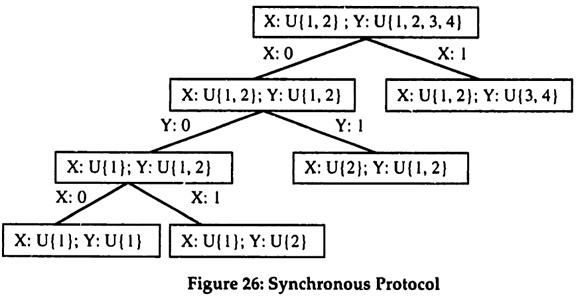
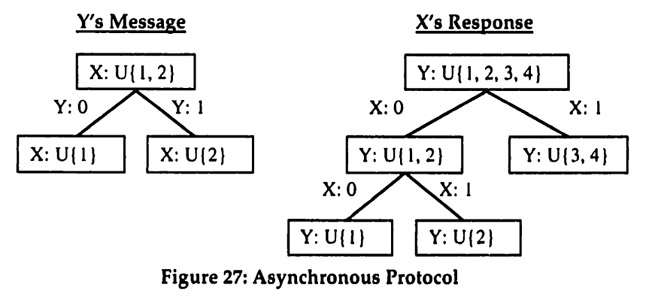
 SY, where Sx = {1, 2,3,4} and SY = {1,2}. This two dimensional state space represents the information observed by the two team members X and Y. Let the set of actions be given by A = {1,2,3,4}. Finally, to keep the example really simple, assume that the benefit function is represented by the matrix in Figure 25, where the action shown for each cell has a benefit of 1 in that cell and all other actions have no benefit. It follows immediately that Figure 25 shows the optimal action for each possible state.
SY, where Sx = {1, 2,3,4} and SY = {1,2}. This two dimensional state space represents the information observed by the two team members X and Y. Let the set of actions be given by A = {1,2,3,4}. Finally, to keep the example really simple, assume that the benefit function is represented by the matrix in Figure 25, where the action shown for each cell has a benefit of 1 in that cell and all other actions have no benefit. It follows immediately that Figure 25 shows the optimal action for each possible state.